LegalFab Compliance Capabilities
Version: 1.3
Last Updated: February 2026
Compliance Framework
LegalFab maintains compliance with applicable regulations and industry standards.
Applicable Regulations
| Regulation |
Relevance |
Status |
| GDPR |
Personal data processing |
Compliant |
| CCPA/CPRA |
California privacy rights |
Compliant |
| SOC 2 Type II |
Security and availability |
Aligned |
| Legal Industry Standards |
Legal data handling |
Aligned |
| MLR 2017 |
Money Laundering Regulations (UK) |
Aligned |
| FCA SYSC |
FCA Systems and Controls |
Aligned |
Note: For detailed AML-specific compliance controls including rule engine, BPM workflows, and screening services, see 08-AML-Compliance.
Data Protection
GDPR Compliance
| Requirement |
Implementation |
| Lawful Basis |
Consent management, purpose limitation |
| Data Subject Rights |
Data discovery, access requests, deletion support |
| Data Protection |
Encryption, pseudonymization, access controls |
| Breach Notification |
Audit logs support investigation and notification |
| Cross-Border Transfer |
Data residency controls |
CCPA/CPRA Compliance
| Requirement |
Implementation |
| Right to Know |
Data discovery and lineage |
| Right to Delete |
Deletion tracking through lineage |
| Right to Opt-Out |
Classification of data sharing |
| Non-Discrimination |
Access controls |
Data Subject Rights
| Right |
Process |
Response Time |
| Access |
Automated data export |
30 days |
| Rectification |
Data update workflow |
30 days |
| Erasure |
Deletion with verification |
30 days |
| Portability |
Standard format export |
30 days |
| Objection |
Processing review |
30 days |
SOC 2 Alignment
Trust Service Criteria
| Criteria |
Controls |
| Security |
Access controls, encryption, monitoring |
| Availability |
Redundancy, disaster recovery, SLA monitoring |
| Processing Integrity |
Input validation, quality monitoring, lineage |
| Confidentiality |
Classification, encryption, access restrictions |
| Privacy |
Consent management, data subject rights support |
AI Governance
EU AI Act Alignment
| Requirement |
Implementation |
| Risk Classification |
AI uses assessed as limited/minimal risk |
| Transparency |
Users informed when interacting with AI |
| Human Oversight |
Human-in-the-loop for high-impact decisions |
| Documentation |
Technical documentation maintained |
Responsible AI Principles
| Principle |
Implementation |
| Fairness |
Bias detection and monitoring |
| Transparency |
AI involvement disclosure |
| Accountability |
Audit trails, clear ownership |
| Privacy |
Data minimization |
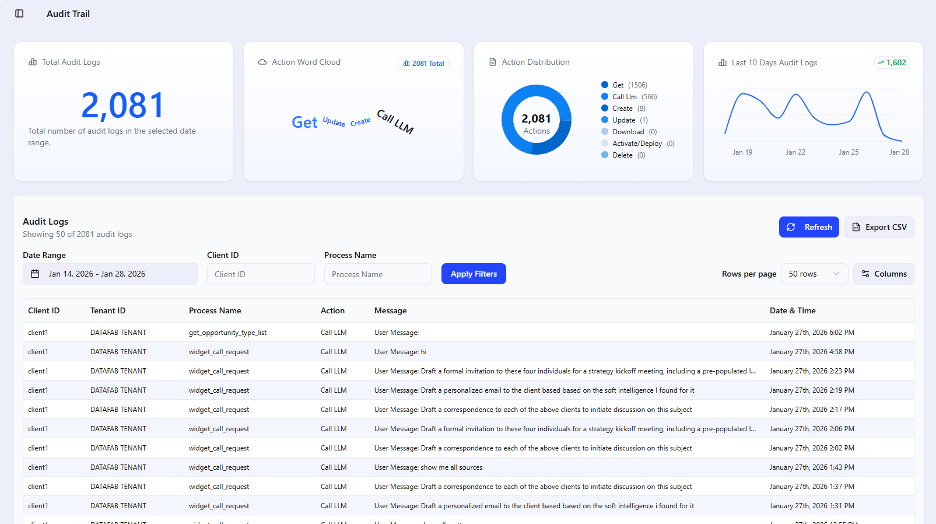
Audit Logging
Audit Requirements
| Requirement |
Implementation |
| Completeness |
All security-relevant events logged |
| Integrity |
Tamper-evident storage |
| Confidentiality |
Encrypted at rest |
| Availability |
Redundant storage |
| Retention |
Configurable per regulation |
Log Retention
| Log Type |
Retention Period |
Storage |
| Authentication Events |
1 year |
Immutable storage |
| Authorization Events |
1 year |
Immutable storage |
| Data Access Events |
1 year |
Immutable storage |
| Configuration Changes |
2 years |
Immutable storage |
| Security Incidents |
2 years |
Immutable storage |
| AML Compliance Events |
7 years |
Immutable storage |
| SAR/STR Filings |
7 years |
Immutable storage |
| Rule Execution Logs |
5 years |
Immutable storage |
Note: AML-related audit logs follow extended regulatory retention requirements per MLR 2017 and FCA guidelines.
Legal Hold and Retention Management
LegalFab manages legal hold and retention policies through metadata-level tagging in the Knowledge Fabric, enabling centralized policy management without modifying source system data.
Retention Policy Framework
| Component |
Description |
| Metadata Tagging |
Sensitive data tagged and classified at metadata level |
| Policy Definitions |
Custom retention policies defined per data classification |
| Lineage Propagation |
Sensitivity tags propagate through data lineage |
| Execution Agents |
Dedicated agents execute retention actions |
Legal Hold Capabilities
| Capability |
Implementation |
| Hold Application |
Apply legal hold to specific matters, entities, or document sets |
| Hold Propagation |
Holds automatically apply to related records via lineage |
| Suspension of Deletion |
Prevent deletion of held records regardless of retention policy |
| Hold Release |
Controlled release process with approval workflow |
| Hold Audit |
Complete audit trail of hold application and release |
Retention Policy Types
| Policy Type |
Description |
Example |
| Time-Based |
Retain for specified duration |
7 years from creation |
| Event-Based |
Retain until event occurs |
Until matter closure + 3 years |
| Regulatory |
Compliance-driven retention |
Per MLR 2017 requirements |
| Privileged |
Extended retention for legal privilege |
Attorney-client materials |
| Investigation |
Extended during active investigations |
Until investigation closure |
Policies trigger based on metadata tags without requiring changes to source systems:
| Tag Type |
Policy Action |
Example |
| PII Classification |
Apply privacy retention rules |
Delete after purpose fulfilled |
| Legal Privilege |
Extended retention, restricted access |
10+ years, attorney access only |
| Investigation Related |
Hold during investigation |
Suspend deletion |
| Regulatory Document |
Compliance retention period |
7 years per regulation |
| Expired Retention |
Review and disposition workflow |
Flag for review at expiry |
GDPR Data Subject Rights Integration
| Right |
Implementation |
| Right to Erasure |
Identify all instances via metadata tags across sources |
| Data Minimization |
Track and enforce minimum necessary data |
| Subject Access |
Locate all data related to subject via unified view |
| Portability |
Export subject data from unified Knowledge Fabric view |
Retention Execution
| Action |
Process |
| Archiving |
Move to cold storage per policy |
| Anonymization |
Remove identifying information while preserving analytics |
| Deletion |
Secure deletion with verification |
| Review Queue |
Flag records for human review at retention expiry |
Retention Audit Trail
| Event |
Logged Data |
Retention |
| Policy Application |
Record ID, policy applied, timestamp |
Policy retention + 2 years |
| Legal Hold Applied |
Matter, records, hold reason, applier |
Permanent |
| Legal Hold Released |
Matter, records, release reason, approver |
Permanent |
| Retention Action |
Action type, record ID, executor |
Policy retention + 2 years |
| Policy Override |
Override reason, approver, duration |
Permanent |
Third-Party Risk Management
Vendor Assessment
| Assessment Area |
Requirements |
| Security Certifications |
SOC 2 Type II or equivalent |
| Vulnerability Management |
Documented patch management |
| Data Handling |
Encryption and access controls |
| Incident Response |
Notification commitments |
| Business Continuity |
Availability commitments |
Contractual Requirements
| Requirement |
Purpose |
| Data Use Restrictions |
Prevent unauthorized data use |
| Confidentiality |
Protect customer data |
| Security Standards |
Minimum security requirements |
| Breach Notification |
Timely incident notification |
| Audit Rights |
Right to review attestations |
Policy Framework
Security Policies
| Policy |
Coverage |
| Information Security Policy |
Overall security program |
| Access Control Policy |
Authentication and authorization |
| Data Classification Policy |
Data handling requirements |
| Acceptable Use Policy |
Appropriate system usage |
| Incident Response Policy |
Incident handling procedures |
Policy Management
| Activity |
Frequency |
| Policy Review |
Annual |
| Policy Update |
As needed |
| Policy Communication |
On hire and annual |
| Compliance Verification |
Continuous |
Data Residency
| Control |
Description |
| Regional Deployment |
Platform deployable in specific regions |
| Data Locality |
Metadata stored in designated regions |
| Cross-Border Controls |
Transfer restrictions per policy |
| Sovereignty Compliance |
National data protection requirements |
Compliance Reporting
Available Reports
| Report |
Content |
Frequency |
| Security Assessment |
Control effectiveness |
Annual |
| Compliance Status |
Regulatory alignment |
Quarterly |
| Audit Findings |
Issues and remediation |
As needed |
| Incident Summary |
Security incidents |
Quarterly |
Audit Support
| Support Type |
Description |
| Documentation |
Security policies and procedures |
| Evidence |
Control implementation evidence |
| Access |
Auditor access to systems (read-only) |
| Personnel |
Subject matter expert availability |

